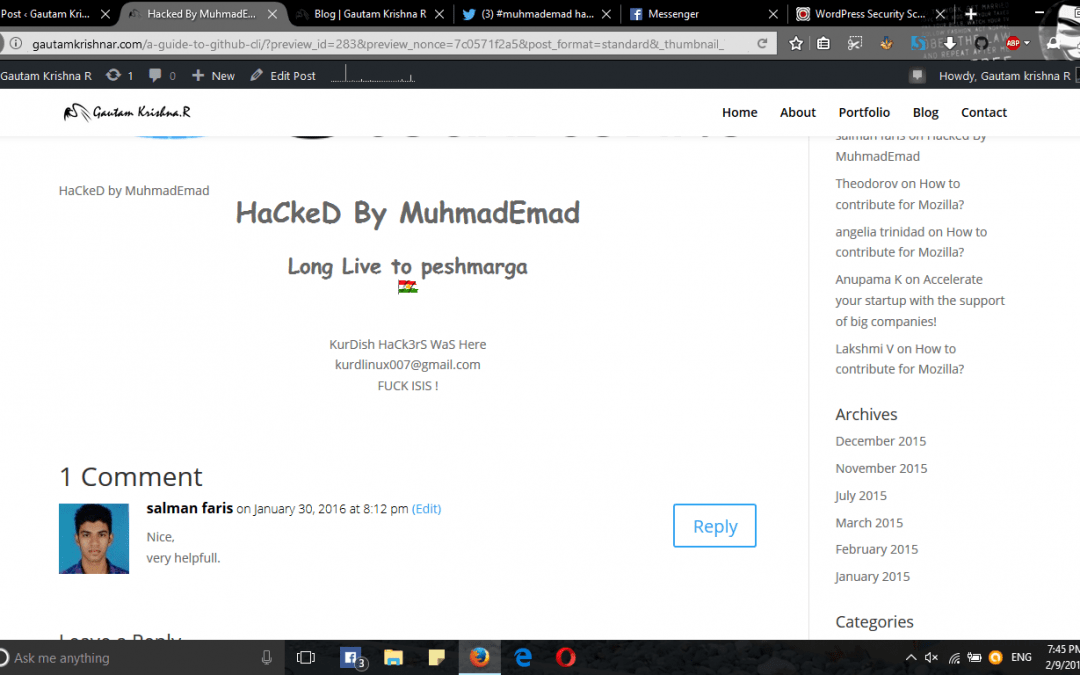
Recently my website encountered an attack by a hacker named MuhamadEmad. First of all a big thanks to him for reminding me about the security loopholes in my website. It was a page defacement attack. He replaced one of my blog post with the page given above.
Looking pretty cool right!… 😀
After doing some online research and discussing with one of my friend and a well known security researcher Hemanth Joseph i found the loophole in my website. I was using an outdated version of WordPress. There was a massive attack on websites that were running the outdated version.. See the news article regarding the issue. Since i was maintaining a Git based backup of my website, i was able to recover from the attack as soon as i found it. I just rolled back to a previous backed up version of my blog and enhanced security by updating the WordPress to the latest version and of course, setting up a gibberish password. Scanned my website using one of the best WordPress vulnerability scanning software named WPScan.
This attack reminded me the importance of securing the website we own, even if it is a personal website So I checked all the access logs of my server. My jaw dropped when i checked the SSH logs of my server, February month’s log itself had a size around 4MB. So i examined the logs by tailing the last few hundred lines of the log. I was actually awestrucked by the output of the command grep sshd.\*Failed /var/log/auth.log | tail --lines=1000. There was thousands of ssh login attempts from hundreds of unknown IPs even on the last few seconds. By doing a reverse lookup on those IP, i found that all of them are originating from Chinese servers. These servers are flooding my SSH port with lots of SSH login attempts. They are always trying to get access to the root account on my server by simply bruteforcing it. I just secured my ssh ports too..
These incidence made me to write this blog. I thought that sharing my experience will benefit others experiencing the same kind of problems. So lets start 😀
How to make WordPress secure?
Since WordPress is one of the most used and customizable CMS, it is one of the best choice for hackers as well. So if you maintain a WordPress blog or website its really important to keep it secure. Even if your website has only a single visitor per month, you must keep it secure. I am not mentioning about the wordpress.com version of the WordPress, i am mentioning about the self hosted version. Since wordpress,com version is maintained and hosted by the WordPress team its secure. Self hosted version allows more customization and configurations while compared to the wordpress.com service. So it is always a choice for the webmasters. So to maintain a secure WordPress installation on your server, you must make sure that the following things are checked:
Use a strong password
Yes keeping the admin password as 1234admin will be easier for you to login, so the hacker too 😀 . Setting a strong password for the website can reduce most of the attacks. Since passwords are the master key to your website, if any of the hacker is able to guess it, you may lose the access to your website. The attacker can even destroy your website. If you are using the same password in your online accounts, that will also be compromised soon. So the importance of setting a un crackable password is very high.
I recommend using password generators available online: https://duckduckgo.com/?q=password+generator&t=hd&ia=answer. Instead of using a single passwords for all your accounts, use separate passwords. Use free and open source password managers to keep track of your passwords. Kee pass is an example. Setting a non standard username for admin account may also add up to the security of the website. Using an email ID instead of a username is a more secure approach, WP Email Login plugin works out best this purpose.
Stay Up to date
Its one of the important way to stay secure. You must check your WordPress version for updates at least once a week. You must upgrade to the latest version as soon as it is released. Since WordPress is an open source project, it have several bugs and loopholes in it. The updates fixes most of them. So it is really important to keep your website updated. You can also enable automatic updates of the WordPress by connecting it with jetpack.
Use 2FA
Setting up 2FA (Two factor authentication) can improve your website security a lot. it will prevent unwanted bruteforcing attacks on your website. You can enable 2FA in WordPress.
Changing your login URL
Every hacker knows that the WordPress login page is available at wp-admin or at wp-login.php. Knowing this location, he can easily brute force it. Installing of jetpack and other plugins allows you to stay out of bruteforce attack. You can change the login page location by using some plugins. Just google it.
Protect core directories and files
Adding server-side password protection such as BasicAuth to /wp-admin/ adds a second layer of protection around your blog’s admin area, the login screen, and your files. Please follow the steps recomended in https://codex.wordpress.org/Hardening_WordPress#File_Permissions. To password protect the directory and fix the permissions. Make sure that your WordPress installation have the necessary permissions only on the files on the webroot.
Use some security plugins
WordPress security plugins can add an extra layer of security to your website. I recommend using Wordfence security. It is one of the most used WordPress plugin that allows you to scan and keep your website secure.
Take backup
Take backup of your website regularly. I recommend Revisr for this purpose: https://wordpress.org/plugins/revisr/
Use HTTPS
You can use https on your website. See the tutorial, It will also add an extra layer of security to your website.
Scan for vulnerabilities
Perform a periodic manual scan of your website using some of the tools like WPScan and other scanners.
Securing your SSH Server
Most of the VPC hosting providers give ssh access to the servers. SSH acess allows us easily manage and configure the server resources. SSH servers are actually one of the most favorite choice for hackers due to its power. If an attacker is able to gain SSH access to a machine, he will be able to perform a complete takeover of that machine. They can even demand some ransom for getting the machine back. So prevention of attacks to your SSH servers are one of the most important tings you must consider while using a VPC. See this page for more info.
Use Public Key authentication
Using private/public key authentication as the authentication method for the server will add an extra layer of protection to your SSH server. Since these type of authentications are difficult to crack without your public/private key file. this is the best type of authentication to use one SSH servers. See the tutorial: https://www.howtoforge.com/set-up-ssh-with-public-key-authentication-debian-etch
I recommend installation of denyhosts, which is a log-based intrusion prevention security tool for SSH servers written in Python. It is designed to prevent brute-force attacks on SSH servers by monitoring invalid login attempts in the authentication log and blocking the originating IP addresses using /etc/hosts.deny and iptables on Linux server.
Installation
Use the sudo apt-get install denyhosts command to install denyhosts
Whitelist your IP
Find your IP address and add it to denyhost’s whitelist. Add IP address of the PC you are using to connect to the SSH server regularly. This step is optional, but it will prevent accidental blocking of your own ip address.
sudo nano /etc/hosts.allow
Add your IP as the syntax below:
sshd: whitelist-ip1, whitelist-ip2, ...., whitelist-ipN
Configure denyhosts
Configure denyhostes by modifying its configuration files:
sudo nano /etc/denyhosts.conf
Set the locations:
SECURE_LOG = /var/log/auth.log HOSTS_DENY = /etc/hosts.deny BLOCK_SERVICE = sshd
Set deny threshold limit for login attempts:
DENY_THRESHOLD_INVALID = 5 DENY_THRESHOLD_VALID = 10 DENY_THRESHOLD_ROOT = 1 DENY_THRESHOLD_RESTRICTED = 1
To block incoming connections using the Linux firewall IPTABLES:
IPTABLES = /sbin/iptables
Restart the denyhosts service
Use sudo systemctl restart denyhosts.service to restart the denyhosts service. See Denyhosts website for more info.
I wrote this blog to share my experience on first ever hacking attempt i received. By using all the tools and security measures above i am sure that you can add some extra layer of protection to your web servers. Still more and more vulnerabilities and bugs are found by the hackers day by day. As a webmaster you need to be up-to-date about the bugs and vulnerabilities of the CMS platform you use.

One of the best blog posts i had ever seen. Thanks for sharing your experience…
Nice post! I admire your civility towards the attacker.
Thank you 😀